Hack to the Future
For many years wars were fought on the sea, on the land and in the air. However a new theatre of war is emerging – cyberspace. The Oxford English dictionary defines cyberspace as: the internet considered as an imaginary area without limits where you can meet people and discover information about any subject. The key words in the definition are “without limits”.
The internet has long been a lawless place quite like a digital wild west, and although agencies do exist such as GCHQ and NCA to help protect users and ‘police’ cyberspace it still remains the fastest growing environment for crime and other related unsavoury acts.
The NCA (National Crime Agency) estimates that cyber-crime costs the UK economy billions of pounds per annum and growing. Last year in its Cyber Crime Assessment, the NCA declared that company directors should address and challenge their management teams to go beyond minimum compliance standards to ensure that rapidly evolving cyber security and resilience threats are anticipated.
For the first time the Office for National Statistics included cyber-crime in the annual crime survey for England and Wales in 2015. They estimated that 2.46 million cyber incidents took place with 2.11 million victims of cyber-crime. That was 36% of the total UK crime figure. As you can see, cyber-crime is big business. So what does it mean for you and your business? More importantly what can you do to combat cyber-crime.
THREATS
So let’s look at some of the more common threats; for example who may be trying to attack you?
Firstly there are cyber criminals – individuals or groups who may be trying to fraudulently make money from selling valuable information. There is a threat from foreign intelligence services and industrial competitors who aim to gain an economic advantage for their countries or companies. A threat could come from hackers who like to infiltrate systems as a hobby or enjoyable pastime, who are quite similar to hacktivists who attack purely for political motivation or ideologies. Finally employees also pose a threat via accidental or malicious purposes.
METHODS
We now know who could be trying to steal or sabotage our information assets but how could they do it? The following are a brief list of methods that could be used; however please do not think that this list is exhaustive as new and real threats are developed each and every day.
Just as fast as technology grows and expands such does the methods to exploit and use these advances for malicious purposes;
-
Phishing - randomly sending emails to large a number of recipients asking for sensitive information or asking them to visit a fake website. The usually method is to ask for bank details etc.
-
Ransomware - computer malware that is covertly installed onto a computer system and effectively holds the company’s information hostage or threatens to publish secure information unless a bounty is paid.
-
Water holing - using a fake website or hacking a real one to exploit visitors and steal information
-
Botnets - create a large amount of infected computers which collectively send out spam emails with viruses attached which can also be used as part of a denial of service attack – an attack to bring down a network by flooding it with useless traffic.
-
Virus - Computer viruses are software programs that are deliberately designed by online attackers to invade your computer, to interfere with its operation, and to copy, corrupt or delete your data. These malicious software programs are called viruses because they are designed not only to infect and damage one computer, but to spread to other computers all across the Internet.
-
Worms - Worms are more sophisticated viruses that can replicate automatically and send themselves to other computers by first taking control of certain software programs on your PC, such as email.
-
Trojan Horse - A Trojan horse is a program which seems to be doing one thing, but is actually doing another. A Trojan horse can be used to set up back door in a computer system so that the intruder can gain access later.
-
Social Engineering - Social engineering manipulates people into performing actions or divulging confidential information. Similar to a confidence trick or simple fraud, the term applies to the use of deception to gain information, commit fraud, or access computer systems.
-
Physical unauthorised use of company assets to gain information - such as breaking into premises, stealing passwords from desk/diaries or using the same Wi-Fi connection.
CONSEQUENCES
What happens if you have data stolen or lost? Novastor a market leading backup provider states that 70% of small businesses which experience a loss of data close their doors permanently with a year and 94% of companies that have a serious data loss end up going out of business, with 43% never opening again and 51% closing within two years of the loss.
Even if the business does survive initially, the reputation is damaged indefinitely. It’s not just small businesses who are at risk; here are a few examples of recent security breaches:
-
Sports Direct – 2017 – Loss of employee personal credentials.
-
Three mobile – 2016 – loss of customer credentials (not financial information).
-
Tesco Bank – 2016 – 20,000 customers had money stolen form their online accounts.
-
Talk Talk – 2015 – 157,000 customer details stolen.
-
Moonpig – 2015 – A researcher was able to access the personal details of any of the company’s 3 million customers via a flaw in its android app.
HOW CAN YOU PROTECT YOURSELF
There are many, many more threats and ways in which the attackers will try and gain access to your information so let’s look at how you can protect your assets:
Emails – who is it from? What’s that attachment? Where does that attached link send me? Be suspicious if you don’t recognise the sender. Do they work for a company you know i.e. does the senders email address match that of the website they say they are working for. A good rule of thumb is – If it doesn’t quite look right, chances are it isn’t!
Passwords – password1 is never a good idea for a password (cue lots of people frantically changing passwords!) anything that is easily guessed should be avoided such as date of birth, surname etc. Think about where you keep your password if you have to write it down. I see so many people with their log on details and password stuck to their monitors on a post-it note – think about it, would you hang your door keys on the outside of your front door?
Physical security – you can have the most secure system in the land but it is only as good as the environment that it is housed in. Ensure only authorised users have access to your network such as access controls, locks, alarms or security for out of hours. Challenge anyone in the workplace who you don’t recognise or looks like they don’t belong there. Don’t think that someone else will do it, plus if they are there legitimately and a new starter then it can be a used as an icebreaker/introduction.
Network security – hopefully you have adequate network protection via your IT department or consultant but no security measure is 100%. Think – what information is important to you? Are your backups recent? Is a copy store off-site and is it secure? Is it process documented and tested? Is there encryption? These are all questions to ask your IT specialist.
THE SECURITY ‘ONION’
Named the Security Onion in relation to the different layers that are present as below:
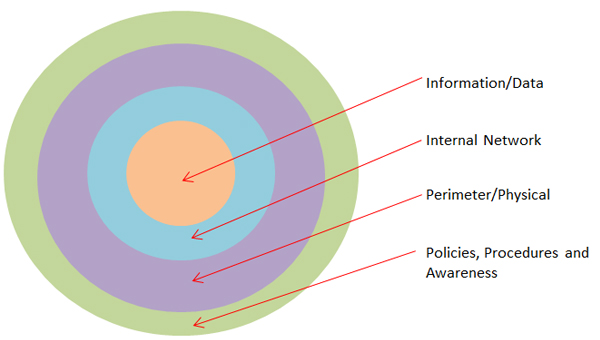

Information/Data
This is the information that the company holds such as customer details, design specifications, employee records. Certain types of file should be password protected or only accessible to certain individuals.
Internal Network
This should detail any system security measures such as; firewalls, antivirus protection or security patches etc.
Perimeter/Physical
The next layer in the onion is the Perimeter or physical layer and as it states this is the physical barriers that prevent unauthorised access to you information. Such things as building access controls, security guards, and secure data centres even down to perimeter fences and security cameras.
Policies, Procedures and Awareness
The systems above are only as good as the people trying to enforce them. All employees should be aware of security policies and procedures, for example what to do if there is an intruder? What should I do with a suspicious email? Who is allowed to access certain data? All these questions should be addressed.
The diagram above is only an example of the different aspects of a layered approach to information security. If you applied it to your own organisation I’m sure you could come up with many more inputs to add even more layers.
You may already have an effective Quality Management System in place but is there anything else you can do? Of course there is, and this is where ISO 27001 – Information Security Management System comes in to place.
ISO 27001 helps organizations secure information assets such as financial information, intellectual property, employee details or information entrusted to them from interested parties and keep them secure.
This is a systematic approach to managing sensitive company information so that it remains secure. It includes people, processes and IT systems by applying a risk management process. Much like the security onion. It can help small, medium and large businesses in any sector keep information assets secure.
Author: Chris Smith, Regional NQA Assessor
